Putting Cryptography Back in Crypto
We’re entering an era in which you can probe a black box and an answer comes out that’s cryptographically guaranteed to be correct without revealing why it’s true – all the computation remains completely private.
Cryptography's in the midst of a zero to one moment; a generational transition from special-purpose cryptography to general-purpose programmable cryptography.
We have previously only had protocols that could perform a single, static operation. For instance, public-key encryption or signature schemes allow the use or proof that I have a unique cryptographic key – but those same protocols can’t also be used for anything else, whether it be constructing a private AMM, a sealed-bid auction, or healthcare data sharing.
Now, technologies are emerging into practical usefulness that allow for truly general computation with cryptographic guarantees. In their limit, these guarantees seem indistinguishable from magic – including proving any computation without revealing any of the necessary data and computing any algorithm over fully encrypted data without ever decrypting the data or revealing the algorithm.
These technologies include zkSNARKs, FHE, MPC, TEEs, as well as others earlier in development. You may be fatigued from hearing these acronyms used as buzzwords each cycle with little to show for it but false starts. We’ve observed the field for years, but have lately been studying it especially rigorously in no small part because its efficiency has improved by several orders of magnitude (OOM) in just a few years. We have confidence the tech is finally ready for major real world applications.
The two broad categories of applications include:
- Proving the correctness of a computation: the scaling solution for Ethereum
- Secure computation over private data: pre-requisite for many of the applications that’d expand crypto’s reach to broader audiences
Though combining privacy with an immutable public ledger may feel like an oxymoron, we believe blockchains and programmable cryptography actually need each other. The former provides seamless composability while the latter enables compute over private data in plain sight.
Neither would be maximally useful on their own but together they unlock truly novel and seriously powerful use cases solving real-world problems, including the following:
- Scaling Ethereum by OOM(s)
- Finance: i) decentralized undercollateralized lending, ii) decentralized debt clearing, iii) other DeFi primitives like sealed-bid auctions, iv) TradFi onboarding
- Digital identity
- Ownership and tokenization of other sensitive info like health data
- A second way to bootstrap networks via vampirism
- Novel social primitives like online speakeasies
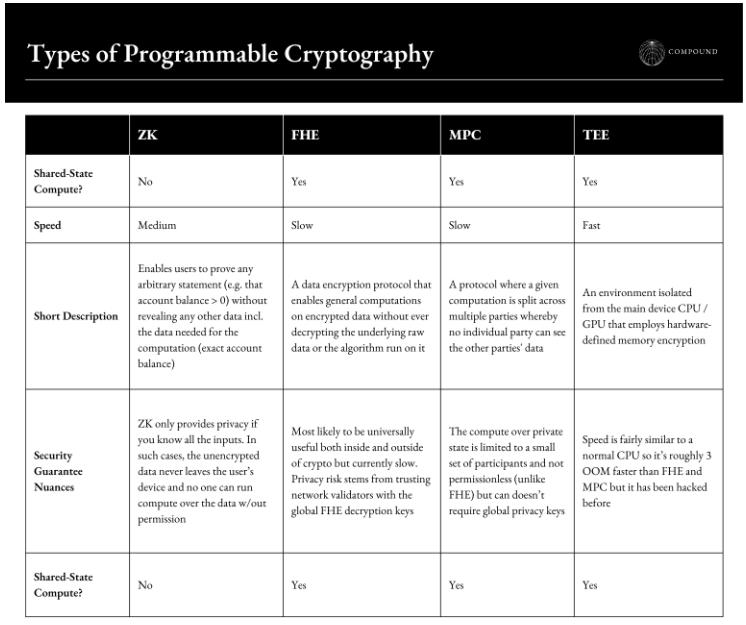
Types of Programmable Cryptography
While I won’t break down the technical details of each technology since others have already done so effectively, the table below provides a high-level overview of their core differences. The TL;DR is that:
- ZK has two use cases: proofs for verification and privacy but only in two-party transactions.
- The others enable private computation over shared state – i.e. when multiple parties can change / use private data while keeping that data private (e.g. the state of a private lending pool or a multi-player strategy game).
- ZK and TEE are the most practical right now given their speed but FHE has the potential to be the most general-purpose, universally useful both in crypto and outside once sufficiently performant.
Given that each protocol has its own security vulnerabilities, design tradeoffs, and speeds, teams looking for privacy solutions will generally combine multiple approaches, as explored in the decision tree graphic below. Thoughtful architectural design can ensure independent vulnerabilities such that if a ZK protocol and TEE both have 1 in 1 million chances of being hacked, then leveraging both technologies together can reduce the likelihood of hack to as low as 1 in 1 trillion. Importantly, the performance drag from combining multiple protocols can be contained by cracked engineering.

Finally, these technologies are coming in waves, moving us in swells towards increasingly generalized programmable cryptography. Special-purpose cryptography has been viable for decades but for very narrow, static tasks → TEEs have been viable for general-purpose private compute for years but have known security exploits → ZK is currently arriving but can only handle single-party private computations → FHE generalizes that to handling any kind of privacy-preserving compute but is still several years out from being viable for complex applications at scale and has some liveness and security drawbacks → indistinguishability obfuscation is the cryptography Holy Grail as it has full black box general-purpose computing capabilities with near perfect security guarantees but is decade(s) out.

Finally Ready for Prime Time
You have likely heard for years now that ZK tech is ready for the main stage, and that NOW is the right time for it. If you’re like us, you’re probably skeptical — if not outright dismissive. The timing may also appear convenient as alt coin prices bleed out, which typically leads to some introspection and reversion towards OG ideals. Privacy’s often atop that list.
So, I spend 600 words providing rigor to why I think this time may be different and the tech actually may be fast, cheap, and easily programmable enough for more general use cases. Moreover, being precise on the question of whether the tech is fast enough is existentially important for startups building here because the timeless lesson is that users won’t sacrifice UI/UX, cost or latency in exchange for better privacy guarantees.
FWIW we also haven’t been shilling this tech every 12-18 months in hopes that eventually we’ll be right. Until recently our belief was that, while interesting, the technology-adoption fit wasn’t quite there yet and we’ve been searching for when that inflection point will happen.
The development of ZK & FHE is one of the many quirks of history where two inventions progressed in parallel and reached maturity at the same time. While both their ultimate lineage can be traced back to the 80s, their direct technological forebearers were introduced ~15 years ago with zkSNARKs in 2011 and the first FHE protocol in 2009. In the time since, they’ve graduated from academic curiosities to now finally being ready for widespread commercial use.
While I’ll save more extended history lessons for others, the bullets below provide a sense of the fields’ trajectories to lay the foundations for exactly where on the exponential we are now.
- Conceived in 2013 two years after the OG paper, Zcash took 2.5min to settle and could only handle the simplest computation: p2p transfers
- In 2019, major breakthroughs to proving algorithms enabled far more general computation, reusable proof setups, and more efficient proving times. This sparked all those zkVMs you’ve heard of.
- Continued academic work on the fundamental proving systems are still discovering efficiency improvements of several times. In all, from 2017 to 2022, the underlying proving systems’ cost and time efficiency improved by as much as 30x.
- Recently, much of the cutting edge work has shifted towards developing compiler abstraction layers so that normal devs can write code without ever even thinking about the underlying technology, automatically translating popular coding languages into the ZK circuit’s mathematical construct or the FHE scheme. That immediately opens up the TAM of developers from 100s to effectively all programmers.
- The last 2yrs have been about progressively plucking the lowest hanging fruit for software optimization for those new general-purpose, developer-friendly execution layers. This software optimization has yielded a further ~10x improvement beyond the basic science work on the underlying proving system or FHE scheme.
All of the work above has yielded eye-popping 170x cost improvements in just 2yrs as the tech has transitioned from PoCs of academic inventions to commercial grade software, or as a researcher said “doing the easiest things first to make the productized implementation incrementally less dumb.”
ZK’s cost curve:
- In just the last year, Risc0 improved proving speed by 5x and costs by 2.5x to now $1 per proof. Given that many transactions can be bundled in one proof, it’d now only cost $200K a year to prove every transaction on Ethereum.
- In the next quarter, they expect another 2-3x improvement. In a year from now, they wouldn’t be surprised if they were 5-10x faster.
- With current time to prove an Ethereum block at ~45 seconds, those improvements would get them to real-time proving.
- For reference, Starknet is already the cheapest Ethereum L2 at 1/10th of a cent
FHE’s:
- As of 2023, FHE was often 1,000x-1,000,000x slower than normal unencrypted compute
- At that time, Inco Network estimated a 1–5 TPS throughput for FHE operations
- FHE developers went from 100 when Zama was founded in 2020 to 4,000 today
- Zama has improved its speed by 100x in the 4yrs since its inception to now supporting 30 TPS for relatively simple transactions like confidential ERC-20 transfers. Their goal is 50+ TPS for arbitrarily complex transactions this year. However, we’ve also heard that truly general-purpose, complex computations in FHE are currently at ~4-8TPS. So more basic apps like a simple AMM can definitely be built today but it's not entirely clear for more complex ones. And, if you want Solana level throughput however, it'll be a little while.
Moving forward, the focus for these fields is currently transitioning from optimizing the software to software-GPU codesign. Integrating with GPUs is leading to 10x cost improvements. True purpose-built ASICs, which are expected to come to market in the next 1-2yrs, could accelerate throughput by another ~5-10x beyond what GPUs provide.
All in all, we’re looking at a ~1,000x cost improvement from ~2017 to 2027.
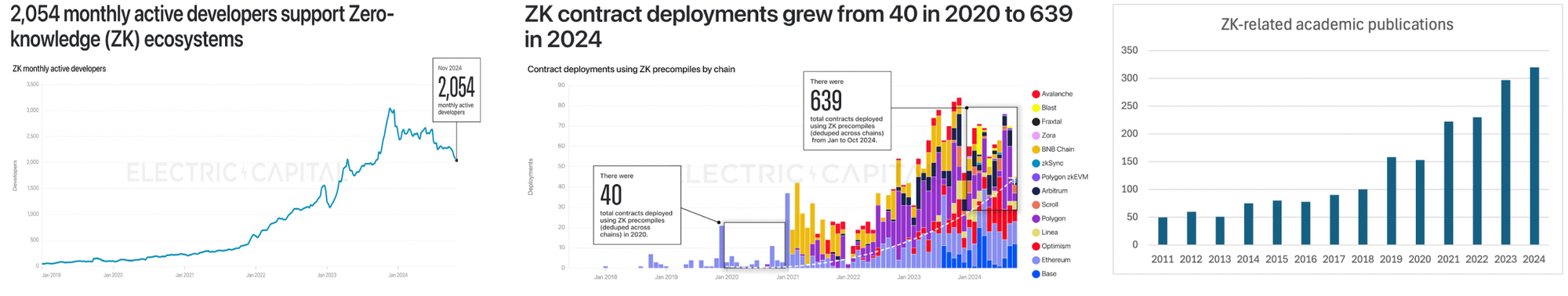

Even considering that the timelines suggested by industry participants are overly optimistic, we’re confident that a key inflection point has been reached and the fields are ready for ambitious teams to start building towards meaningful real-world applications. The compiler abstraction layer development makes it so that we should see rapid growth in the design space as developer friction melts away.
The below explores the applications we at Compound are most excited about.
Applications
Proving: Don’t Trust, Verify
Blockchains are all based around excessive redundancy. They achieve decentralization guarantees by having a minimum viable set of machines (definition of minimally viable is open for interpretation) independently running and re-running the same computations. The trade off is of course speed and computational efficiency.
ZK enables verifiable correctness whose proofs never expire. It’s the only tech that largely solves the tradeoff by proving the computation immutably so that nodes no longer have to re-execute transactions or re-do all the work to verify them.
As detailed in the section above, that reality is rapidly approaching. zkVM leaders are confident that within a couple years:
- It’ll cost $100K a year to prove all Ethereum transactions
- More blockchain computing will happen off-chain via verifiable proofs than on-chain
- Real-time proving is inevitable. Indeed, the RISC0 CEO said he’d be “very happy to bet someone that before January of next year, real-time proving will be a practical reality.”

If this comes to pass, the crypto landscape may look fundamentally different. Ethereum may have a path to close the TPS gap with other high-throughput chains.
The implications don’t stop at Ethereum finally achieving its scaling roadmap. Block space is currently fixed, ironically causing gas fees to spike when people actually want to use the network. However, ZK can verify nearly arbitrarily large bundles of transactions for the same cost so gas prices can stabilize, de-coupling them from demand.
Together, these outcomes would likely imply lower burn, lower albeit more stable Ethereum L1 revenue and would shift its primary competition to the Celestia’s of the world, serving as a settlement and DA layer as opposed to a high-fee execution environment.
In the longer-term, real-time proving alongside shared sequencing may even fix Ethereum’s fragmentation issues by introducing synchronous composability.
Note that these programmable cryptography technologies aren’t specific to Ethereum. It’s just that user expectations for Ethereum execution speeds are lowest. Not only not drag performance down like they would Solana but ZK is actually the solution to speeding it up. Likewise, these technologies aren't even specific to blockchains, but will be applied to them before their far faster centralized database cousins. Indeed, Big Tech companies, DARPA, etc. are already building their own implementations and SDKs.
Considering all the above, it’s not surprising that zkVMs are currently seeing the most demand for uses like proving EVM rollups, Eigenlayer partial withdrawals, and aggregation of proofs from various proof systems.
Finance (i): Undercollateralized Lending
Undercollateralized lending remains one of the holy grails to unlock in crypto. It constitutes effectively 100% of the world’s $140 trillion traditional debt markets.
Yet, undercollateralized lending effectively doesn’t exist in DeFi.
Over time, we expect to continue to see new forms of debt collateral move on-chain beyond Treasuries. We're beginning to see the early instantiations of this with real estate investment products being tokenized and eventually hopefully the collateral itself will be issued natively on-chain. Regardless of broader markets’ timelines, even the most immediately relevant TradFi market that doesn’t require any sophisticated collateral tokenization – unsecured business loans – stands at $5 trillion.
The lack of undercollateralized lending leaves DeFi mind-numbingly inefficient with capital. Borrowers must lock up capital representing over 150% of the value of the loan they desire. In traditional markets, borrowers only have to pony up roughly 60% in assets for the loan. That means if DeFi achieved similar undercollateralized lending standards as traditional markets but in a decentralized way, today’s DeFi capital base could support at minimum 90% more lending with the same level of risk. In reality, it’d likely increase lending by many multiples because increasing capital efficiency by that much would fuel new demand and money velocity.
Undercollateralized loans have been tried in crypto, but only in CeFi markets. That reached ~$60B in 2022, but plummeted 90% the following year as participants like Celsius proved wildly inept and often outright fraudulent. Ironically, they avoided using the open, immutable ledger their business is based on, due in large part to lack of privacy. Instead, they stumbled around in a drunken, blindfolded orgy where a handful of major players carelessly threw money at anyone who wanted it. And, because they were all privately negotiated handshake or OTC deals, nobody knew who owed how much to whom. The daisy chain of leverage unwound quite disastrously and we haven’t seen this type of credit expansion return since.
What was missing? Privacy-preserving, verifiable transparency.
Despite prior desires to build solutions, the technology to provide permissionless, decentralized undercollateralized lending hasn’t existed until now.
The essential technological unlocks were ZKP broadly and zkTLS specifically – a novel tech that acts as a secure bridge from private Web2 website data like bank balance or Uber rating to Web3 by making HTTPS verifiable.
zkTLS enables users to prove to an oracle that’s present in real-time that data accessed via a TLS web session originates from a specific API or website, while revealing only information desired. More specifically, oracles or third-party nodes attest their digital signature to correct HTTPS requests and responses. Using the encrypted response and the digital signature, the user's device then generates a ZK proof that the data was present. [For more detailed explanations see these resources.]
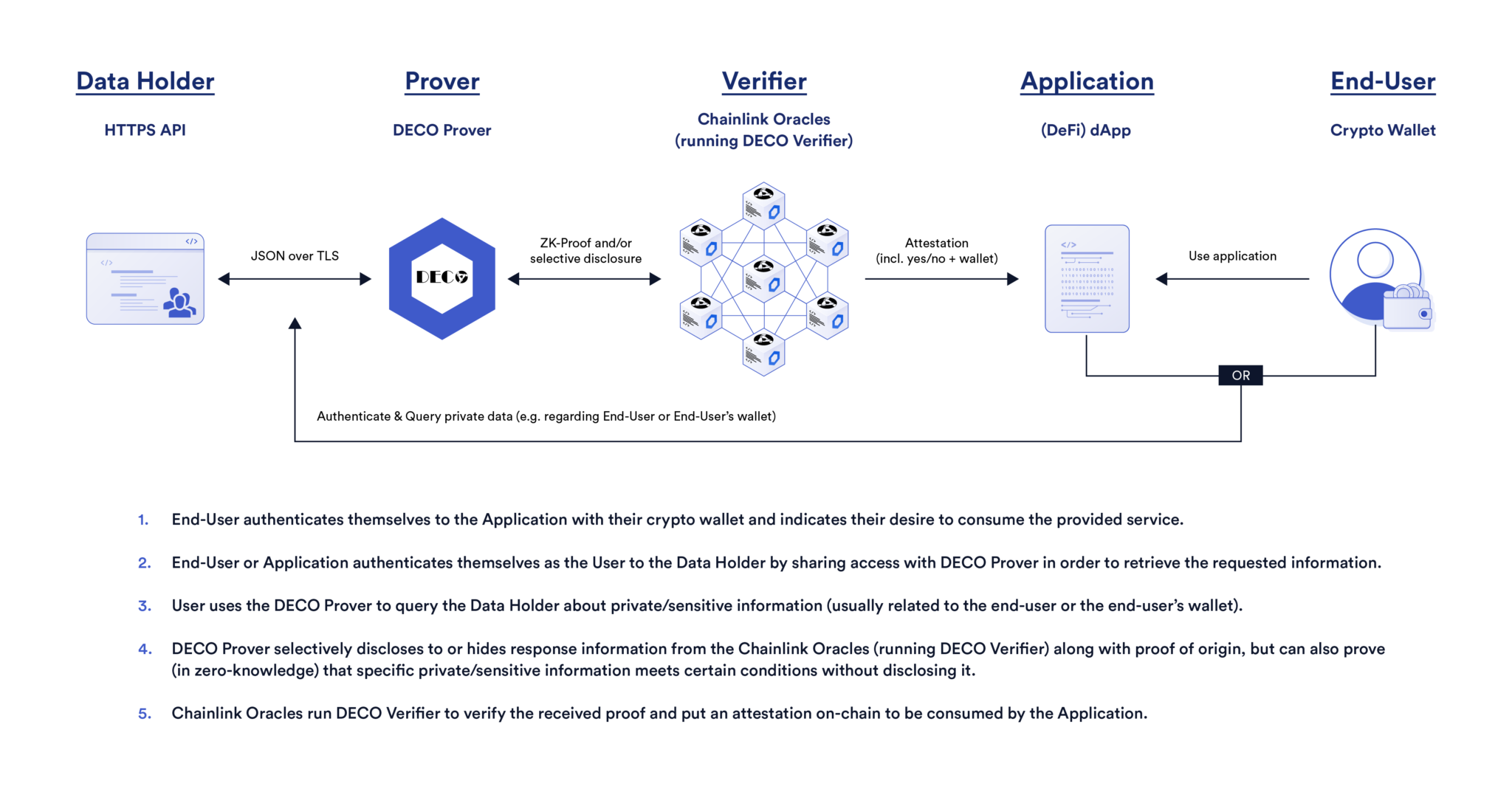
With roots back ten years and a major advancement in 2019, the tech has recently reached maturity. Startups have popped up exploring various use cases as discussed throughout the rest of the post.
Chainlink acquired that pioneering developer and built an undercollateralized lending PoC with Teller. They now offer various privacy tools like ID or sufficient funds checks for DeFi in live sandbox mode.
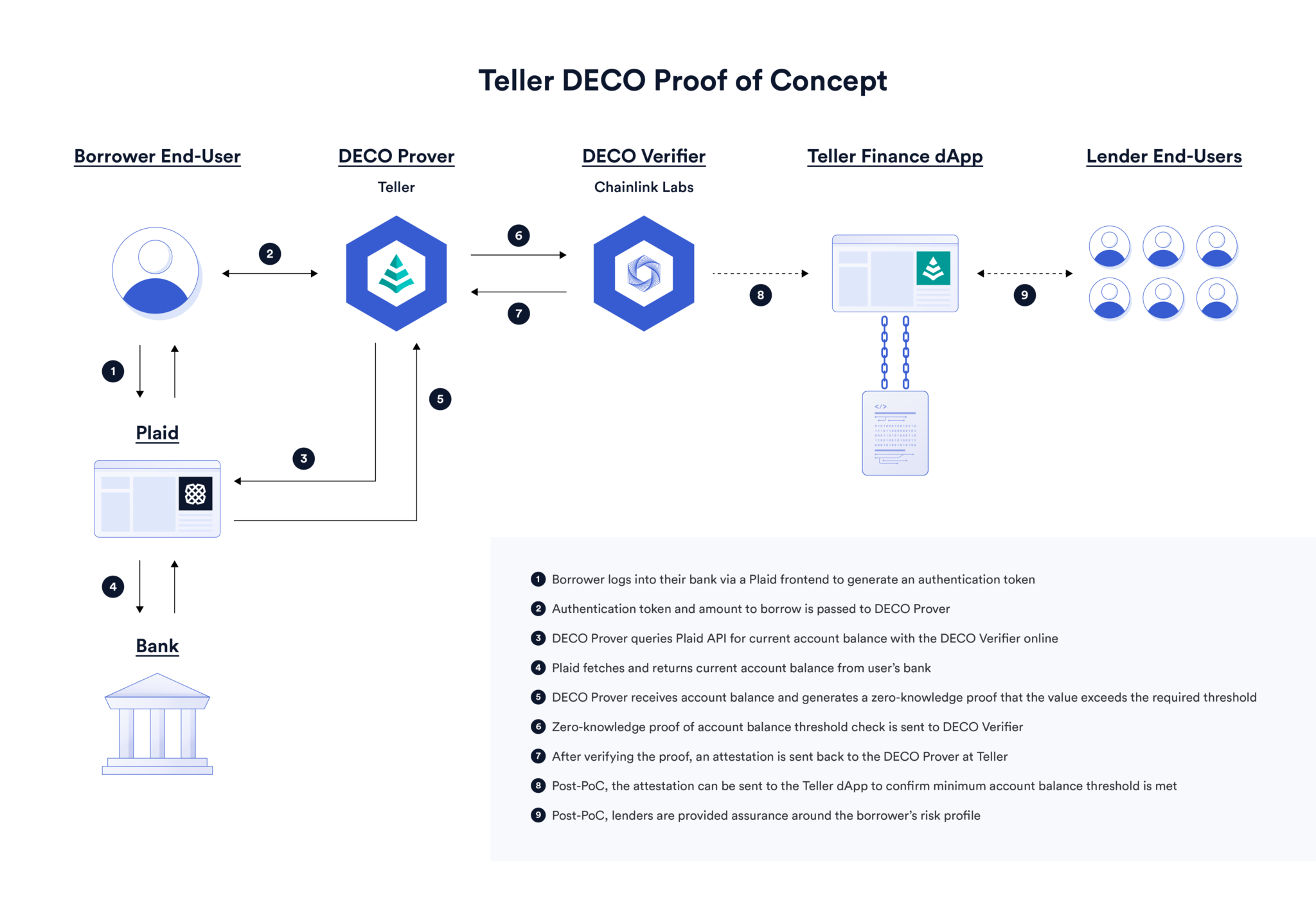
Accountable is taking this PoC further by attempting to build a meshed network of borrowers and lenders so that participants can check with the others whether a borrower has undisclosed liabilities.
They also aim to integrate with existing lending platforms (CeFi and DeFi), Prime Brokers, etc. to cover the broadest possible surface area. The more major participants join the network, the more likely it is that a borrower’s liabilities are fully accounted for… the stronger the incentive not to lie or act irresponsibly… the more likely it is that future lending will occur on the platform.
Such a network should also enjoy positive selection bias – the participants most likely to desire such a platform are the ones most likely to act honestly.
The exact scheme of how they handle a scenario where a borrower has a loan from Lender A and wants a new one from Lender B can be seen below.

With all this said, they’re not attempting to solve the recourse problem – blockchain doesn’t magically solve the need to bang on someone’s door with a warrant if they’ve ghosted your delinquency notifications. That risk will be priced into the platform.
It also still relies on annual IRL audits of financial statements to place further pressure on honesty.
From ZKP of balance sheets to networked attestations to positive selection bias to IRL audits, undercollateralized lending protocols must do everything possible to reduce the core problem of information asymmetry and enhance incentives to proper behavior. Otherwise, the interest rate for undercollateralized loans in DeFi would be impossibly high to compensate for the risk.
By leveraging all these techniques, it may be possible to instill the desperately needed transparency to opaque, private markets. The networked sharing of aggregated, non-specific data provides a comprehensive overview of all off- and on-chain assets and liabilities. Lenders can make informed decisions and all parties can retain privacy.
We march away from unaudited financial statements and screenshots towards live ZKP verification of borrowers' solvency and trading exposures.
Beyond replacing shadow networks of untrustworthy CeFi lenders with a far more transparent system, platforms such as Accountable are useful for:
- Live 24/7 trustless proof of reserves for exchanges, etc.
- Traders that can’t give up positions, sizing, etc. (first major client being HFT)
- Maybe one day, if more collateral can natively be controlled in smart contracts, normal consumers will look to these protocols for permissionless undercollateralized loans. Indeed, undercollateralized lending is the main lever for investment in future productive capacity and the only option for those that aren’t already wealthy or own an excess of assets.
Finance (ii): Decentralized Debt Clearing
Bitcoin was famously created during the GFC as an alternative to the traditional banking & monetary system. But, neither it nor any other crypto or FinTech technology has been capable of fulfilling that mission. Bitcoin, Venmo, USDC, etc. are all p2p electronic cash innovations for bilateral settlement.
Actually disrupting the foundations of the traditional banking & Federal Reserve system requires something more radical: decentralized debt clearance.
The economy’s a massive meshed web of people owing and accepting debts from one another. I may owe you $20 for spotting dinner last night, your employer owes you $2K for salary, you must pay rent by a future date, etc. Conveniently, the network of debts has a somewhat circular or cyclical structure, as caricatured in the graphics below. When you include common liquidity sources (e.g. bank money) into this mesh of transactions, then every payment can actually be expressed as a cycle. Together, this means all the debt in the economy can be dispelled with far less liquidity than is collectively owed.
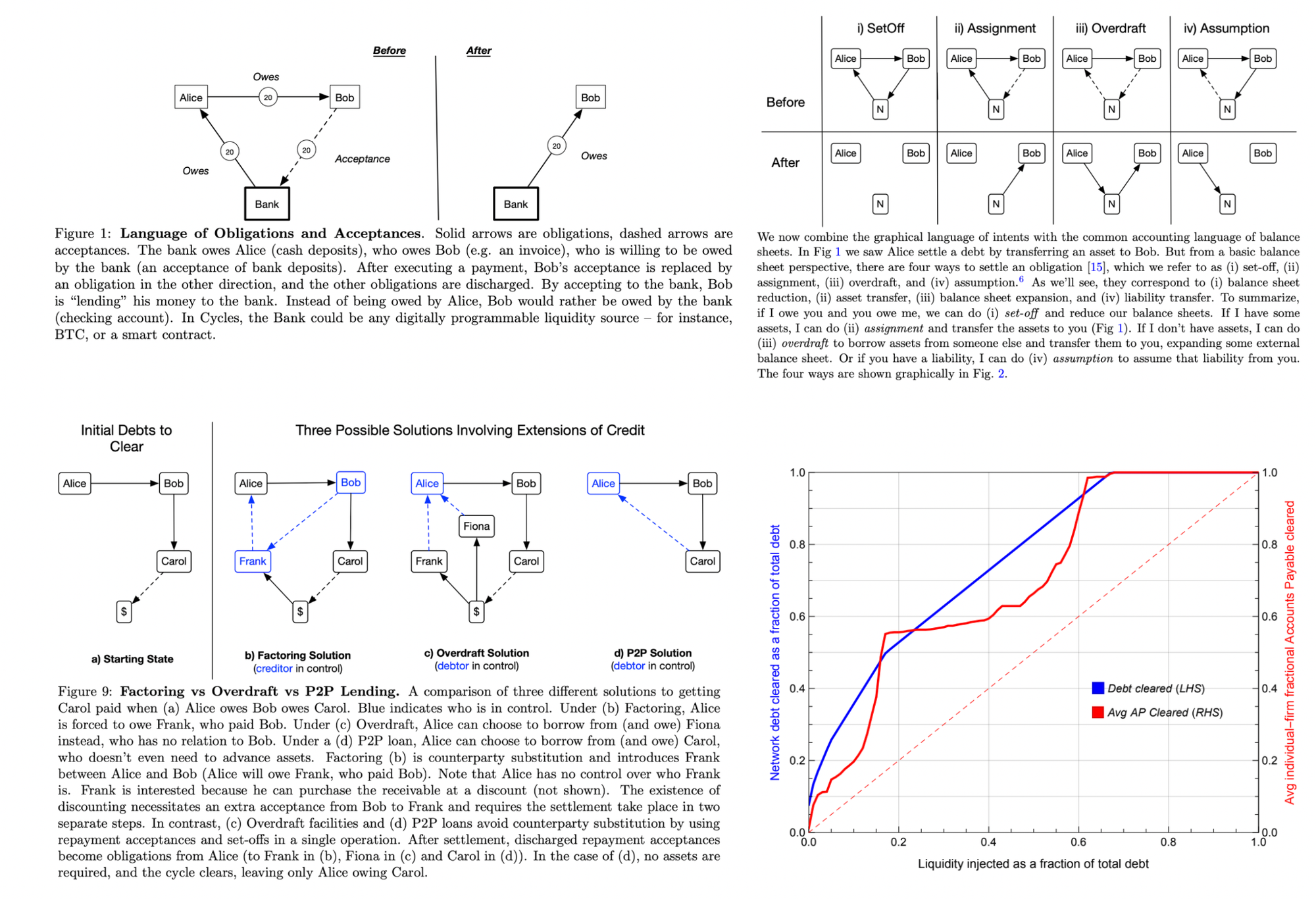
Debt clearance requires a global view and control over the graph of obligations. For centuries, the right to do so has been tightly safeguarded by closed banking clubs. A small number of massive “clearing houses” gather around a table to cancel out all the redundant dependencies across their respective networks with the least amount of capital. Banks can typically get away with capital ratios around 10%.
However, the modern commercial banking and Federal Reserve system wasn’t designed from first principles to be maximally efficient and robust. Rather, it was hobbled together over hundreds of years of happenstance and political deals, leading to occasional liquidity freezes and crises (see this book for an excellent account of the topic).
Until now, the technology didn’t exist to clear debt in a decentralized, intermediary-free manner (at least beyond the scale of small villages). That requires
- a freely accessible, immutable ledger that records the global network of obligations
- in a privacy-preserving and secure manner
- and can settle the debts instantaneously
- according to a graph algorithm that’s optimized to clear the debt maximally efficiently
Spoiler, that’s exactly what Cycles is building.
Users’ debts are encrypted (including both the amount and the counterparties) and then submitted to the protocol’s blockchain. They can also add certain preferences like assets they’re willing to accept (from USDC to bank money to SOL) and the accounts / protocols they’re willing to borrow to / lend from.
In regular intervals, the encrypted intents are fetched by a ZK-TEE system that decrypts them into the corresponding graph. The graph algorithm finds the settlement solution that discharges the collective debt with the least capital. The solution is encrypted and a ZKP is generated that validates the correctness and integrity of the graph algorithm’s output. Both are then submitted back to the blockchain, at which point all the debt accumulated in that interval is settled in a multilateral atomic settlement, and the users see the final results.

This basic configuration described above can be greatly extended. All kinds of DeFi protocols and liquidity sources can be integrated into the graph. And, since every node in the graph is a smart contract corresponding to a balance sheet, every node is a programmable liquidity source, a lending protocol, a bank. That programmability enables automatic, maximally efficient loan drawing and repayment. For more details on extensibility, see below:

In short, the network view opens opportunities to build a new clearing system from the ground up to save liquidity which could help people ease cash flow stress, working capital costs, late payments, reducing risk, etc. They’re first targeting trade payment networks. Who knows, maybe they’ll eventually even draw in SMBs and your average Joe.

Finance (iii): Other Novel DeFi Primitives
- ZKP2P as a trust-minimized, instant on/offramp protocol that uses zkTLS to confirm a KYC’d account with Venmo, Revolut, etc. No fees, no new ID checks, in under a min.
- Confidential and compliant p2p transactions: think Tornado Cash but verifying that not on sanctions lists or have previously committed crimes without remaining private. Privacy and accountability no longer has to be a false dichotomy
- The first on-chain, fully KYC/AML-compliant dark pools and privacy DEXs have emerged. Dark pools account for ~15% of US equity trading and 51% happens off exchange in “dim pools.”
- Full MEV resistance for DEXs
- On-chain Sealed-Bid / Blind Auctions: bidders submit their bids privately and the individual bids are only revealed once all have been submitted. Because no one knows each others’ bid amounts, participants have no game theory incentives to bid any amount other than their willingness to pay (WTP). It’s of course useful for NFT sales and collateral auctions, but could also help solve retail participation in private funding rounds. Community members bid on round FDV in a sealed-bid auction. Then tokens would be distributed per a predetermined mechanism (e.g. clearing price set to median bid and tokens distributed equally to those that bid above that price). Participation could even be gated to true network users (not those just looking for a quick buck) by ZK proofs of network usage, etc.
- Shared-state privacy tech allows exchanges, lending protocols, etc. to share threat intelligence data with one another to identify and ban bad actors while maintaining the data’s privacy. Similarly, bank fraud detection machine learning algorithms could use data pooled from multiple banks.
Finance (iv): TradFi
Privacy and composable identity are basic prerequisites for effectively all TradFi use cases. The only industries with (debatably) more sensitive data are healthcare and government. Indeed, JPM stressed that “realizing blockchain’s transformative potential hinges critically on addressing institutional-grade privacy and developing composable, privacy-preserving identity solutions.
For the first time in crypto’s history, permissionless blockchains can simultaneously offer robust privacy and identity / compliance / accountability. A recent new primitive particularly suited to TradFi is Circle’s new confidential ERC-20 framework for “Compliant Privacy” that enables the following features among others:
- Delegated viewing: Permission to view balances can be granted to specific parties like auditors, regulators, and/or law enforcement without compromising user privacy.
- Programmable transfer rules: Regulatory compliance measures (like anti-money laundering rules, transfer limits, etc.) can be programmed at the smart contract level.
To be clear, TradFi adoption will occur gradually and in staged sequences, starting with those that benefit most immediately. Companies that make their money by facilitating and/or exploiting retail degeneracy like Robinhood and Citadel are already leaning in.
Next come more traditional but forward leaning institutions like VanEck, Franklin Templeton, and even BlackRock. They’ll start with largely permissioned chains and off-chain activity like ETFs but will gradually dip their toes into permissionless on-chain activity.
Early demos of TradFi asset tokenization have hinted at tangible benefits. E.g. Franklin Templeton and Hamilton Lane reported 1,000x+ decreases in costs for agency transfer settlement and share-classes investment minimums vs legacy systems. But again, adoption’s hindered. JPM wrote a 60-page report on asset tokenization and their expectation for it to see exponential growth to trillions of dollars as well as all the dry TradFi stuff like fund administration, secondary fund trading, etc. At each turn, they stressed the need for privacy.
Visa and others have shown a proclivity to use the cheaper and more programmable payment rails that are stablecoins but corporates have hesitated because they don’t want to reveal their business partners / suppliers, the contractual terms of their agreement, their employees’ individual salaries, etc.
The repeal of SAB 121 means that banks now no longer have to record crypto held in custody on behalf of customers on balance sheet. This makes it far more capital efficient for them. Citi and State Street immediately launched custody offerings.
A final, less discussed use case is invoice factoring. Large corporations like Coca-Cola employ hundreds of smaller, regional trucking companies to deliver their products. Given the operational complexity and sheer volume of business, the large corporations often impose a 30-60 day settlement period on their invoices. Those SMBs often turn to the $3 trillion invoice factoring market, for a fee of course.
However, the current manual process for verifying invoices requires trucking companies to share sensitive login and password so the underwriting bank can log in directly and check the validity of a delivered invoice, creating security risks and slowing down the validation process. By employing zkTLS, companies can securely provide proof of invoice delivery without revealing confidential information. Further in the future, if corporates and financials move on-chain, the regional trucking co’s might submit their proof of invoice to a smart contract and receive near-instant payment, all without human intervention.
Again, we at Compound see TradFi onboarding as a glacial process but one that can only begin with compliant privacy.
Identity
Our lack of personhood on the internet feels like one of the more fundamental problems still unsolved by either Web2 or Web3 players, and one that will get exponentially worse with GenAI. We have identities on individual sites – you have your pfp on Instagram and your work colleagues know the icon on Slack is you. And, Google & Facebook’s login services help decrease the number of passwords we have to remember to enter our own fiefdoms.
But nothing links our physical personhood to the digital realm and nothing carries with us across each walled garden.
GenAI already making fake content infinitely scalable and indistinguishable from real content makes these needs acute and immediate.
En route to its $11B FDV, Worldcoin famously got 10M people to pilgrimage to The Orb to have their iris scanned and their unique number minted.

Beyond feeling a tad dystopian, that solution doesn't tie you digital identity to your physical one – it merely mints a random number that proves unique personhood.
The Orb is also now entirely unnecessary.
Startups have built tech when you take a picture of your passport & scan its NFC chip and it generates a ZKP verifying your identity whenever you need it. None of your passport data ever leaves the phone or passes through a server where it could be intercepted. Instead, it generates a ZKP of uniqueness by hashing identity metadata and adding it to an on-chain ZK registry. You could also selectively disclose specific information (e.g. personhood, citizenship, that you’re over 18).
Over time, these startups will make this identity check practically unfakeable by combining multiple other forms of ID like a FaceID selfie powered by ZKML to log into the app, a zkTLS-based email login, a proof of current address (e.g. a picture of an electricity bill), social graph attestation, etc.
With over 90% of the world’s passports already verifiable on Rarimo, these identity products are starting to catch on. Worldcoin has 10M users, Human Passport has 35M, and the city of Buenos Aires rolled out ZK-backed digital identities to all its 3.6 million citizens, becoming the first government to officially hand off full ownership and control of digital credentials to its residents. A similar solution exists in India.
With these solutions, your identity can be encrypted on-chain, suddenly making identity a composable primitive in blockchain that you can query from a smart contract.
So what can we do with this tech?
- Sybil-resistant crypto airdrops that could be programmable beyond unique personhood to include trading volume, KYC, etc.
- This concept could be expanded to aid or government distributions, which could be distributed with nearly zero transfer costs to anyone with a smartphone based on citizenship, socioeconomic status, or anything else that you want to prove.
- Rewards for loyalty, fans, citizens, etc. (e.g. a concert like Lollapalooza Argentina could offer preferential access for citizens of the home country)
- Verifiable web: we may be moving towards a future in which every time you do something online you automatically cryptographically sign it with your unique identity key, remaining pseudonymous if you desire but marking that a human in fact wrote the Tweet, authorized the stablecoin transaction, secured the Resy reservation, etc.
- Businesses can also be registered and verified for a range of products from the bank. While Buenos Aires is leading with citizen credentials, pilots are already live across Latam using the same tech for businesses to open bank accounts, receive notarized approvals for licenses and more.
- A backdoor route to penetrating the cybersecurity market. As of 2023, 75% of security breaches are caused by mismanaged identity, access, or privileges. One 2020 report found that 79% of organizations had an identity-related breach within the previous two years. Fixing identity solves much of traditional security issues.
- Edward Snowden- or Boeing-style whistleblowing / leaks in which the person can prove their credentials without revealing their full identity
- Digital tamper-proof voting
- Rarimo's Freedom Tool supported anonymous voting apps in Russia, Iran, and Georgia for 60k+ users. To avoid punishment, those countries’ citizens prove their citizenship without revealing their identity. The Russian version is led by opposition leaders and received 15K downloads in its first 24hrs – a record for decentralized social apps.
- This could be expanded to non-autocratic nations. Yep, you guessed it – Argentina’s exploring this.
- It’s also being applied to improving DAO governance
Going Beyond Proving Personhood
Over time, an identity platform could earn user trust to host ever-more of people’s digital records, credentials, and personal data in fully encrypted form.
We at Compound are particularly interested in the health angle. We see futures in which people increasingly take their health into their own hands with biohacking and the amount of health data each person generates grows exponentially from genomes to EHR records to cancer sequencing to Oura rings and biochemical wearables.
We also can imagine a future in which people trust cryptographic guarantees of data stored on their secure iPhone more than centralized servers.
Want to guess how many times HTTPS has been hacked?
Never. As in: not once, ever. In its 30 years of securing all internet traffic every second, globally.
It may be naive to assume that general purpose cryptographic protocols will be as unbreakable as special-purpose ones. But it’s safe to assume they’ll have a far better record (especially when combined with the iPhone’s security) than healthcare servers’ continual data breaches. Indeed, the data would never leave your phone and never get decrypted.
As such extreme security guarantees permeate everyday life, it isn’t hard to imagine user behavior slowly changing, just like people no longer think twice about using their credit card to shop online.
We at Compound backed Computable Labs (fka Datamined) under a similar premise in 2016, but these privacy tools didn’t exist and user behavior wasn't ready. It still may not be quite ready, as it takes years for people to become fully habituated to new technological paradigms and this paradigm has barely even begun.
But soon, the three futures may intertwine to enable the creation of an open market for bio data.
Biotech suffers from severe lack of quality data and heinously bad data liquidity – it’s siloed in walled gardens like hospitals. It’s so limited that biobanks sell packages of just genomics & EHR data of 10K people for $1,000 per person. A truly comprehensive digital twin could plausibly be worth $10,000 per person.
To monetize the data that people already produce in their natural life for free for thousands of dollars, they could tokenize all their health data on a fully encrypted chain and then lend it into data pools as they see fit.
In a PoC of this, a privacy chain demo’d a partnership with a genomics company where the user can specify exactly what their data may be used for and see each time the genomics researchers computed over the encrypted data.
Here’s where the blockchain’s immutable, public ledger may be crucial to driving user behavior. The data doesn’t evaporate into the ether of a centralized cloud where the user never sees or hears about it again. Quite the opposite: the user can see with their very own eyes a history of every time the encrypted data was used, for what, when, and by whom. This sense of control would inspire psychological safety, just as with DocSend’s original value proposition.
That same tangible, visual record simultaneously solves a problem that hinders charity funding: once people send away their money, that’s it. The joy of doing good doesn’t come from clicking ‘Send’ but by viscerally feeling its impact by seeing it first hand. With this solution, users could see exactly what research their data is contributing to in real time and automatically get a report back when their data was involved for example in the curing of a cancer.
Altogether, this could create a sustainable self-funding mechanism to dramatically scale human data for biology research while allowing everyday people to monetize the data they create for free. It’s like DePIN with your body.
Moreover, if a solution became the aggregation layer of all the users’ data, then it could expand to telehealth services like being their digital doctors, coordinating enrollment in clinical trials, etc.
Ultimately, the more capabilities a solution adds together (whether it be identity, health data or otherwise), the closer it looks like a “go bag” across digital realms or superpowered wallet / browser. That’s how to go from a feature disguised as a company to a superapp.
Bootstrapping & Vampirism
Crypto famously introduced tokens/financialization as a solution to the cold start problem to bootstrap networks from scratch. zkTLS adds a second solution to that toolkit. By enabling the tapping into existing troves of Web2 data and credentials without requiring external API access, brand new networks can port over the very data and graph connections that make incumbent network effects exponentially valuable for free and without permission. This may even test the assumption that network effects and being first to PMF are untouchable.
- A new DEX might offer zero fees to power users of Coinbase or Binance
- ZKP2P is building a ticket resale marketplace on top of Ticketmaster, combining ZKP and an on-chain smart contract to provide secure escrow.
- Decentralized Uber is an OG idea for crypto that I remember telling my friends about in the 2017 ICO summer. Out with their 30-40% rent-seeking take rate! Or, less revolutionarily, your margin is my opportunity. While this idea never caught wind, a new startup called Nosh is using zkTLS to enable restaurants and drivers to import their reputation data from services like DoorDash. They bootstrapped to 100 restaurants in 1 week, and the drivers & restaurants like it so much that they now have 40% supply-side exclusivity. Drivers and restaurants can use Nosh to receive both Nosh and Uber Eats orders without leaving their website.
- A Web3 social network could vampire attack an existing social platform by rewarding influencers with large followings
- An applied cryptography researcher proposed privacy-preserving contact discovery for new social networks like Bluesky. Users from an existing social graph like Twitter can find each other and form a new graph without publicly exposing their social graphs or linking accounts.
Other Novel Social Primitives
Social media platforms today can address two of the following: proving your identity/credentials, reaching large audiences, and a controllable degree of privacy.
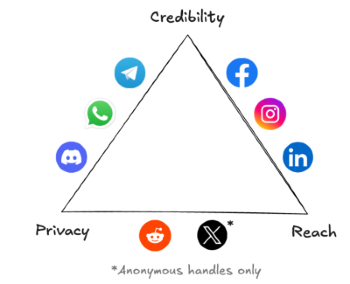
None nail all three at once. Networks like Instagram or LinkedIn enable mass reach but represent maximally public and permanent displays of yourself. People self-censor and post overly polished personas accordingly. Reddit also enables reach but pseudonymity with no means of proving real-world credentials means that users can only build social reputation by posting hundreds to thousands of times and collecting badges. Twitter is/was an interesting middle ground but is diluted by low-quality interactions given the lack of a gating mechanism. Meanwhile, messaging apps of course enable privacy but you can only reach those already in your social graph.
Some teams are introducing tech discussed in this post to better solve the trilemma. Speakeasy extends locality to cyberspace. It employs filters that resemble those used implicitly in the physical world to enable online spaces that admit only the “right” users while blocking the unwanted. Doors to online spaces that are by default unseeable but that open automatically for the right people.
Such filters could include that you’re a member of a specific gaming guild or a certain political activist or working on and posting about novel ZK-based social media primitives. With advanced AI these smart filters could represent increasingly comprehensive and high-dimensional latent spaces of your online presence – i.e. better representations of you.
The crypto industry is an interesting test bed where dev coordination happens uniquely openly and permissionlessly – anyone can join a protocol’s Telegram group and see how the team thinks about product development and provide feedback in real time. But, these groups quickly get overrun by hundreds or thousands of accounts and rapidly lose any value. With solutions like Speakeasy, they could easily be gated to permissionlessly include or even invite people who meaningfully constructively contribute to the protocol’s future.

Cursive is exploring the conceptual digital equivalent of pheromones – chemical signals that you’re constantly sending out to sense for human connection and compatibility. You can emit lightweight, privacy-preserving signals about who you are, your interests, and what you want. This potentially sensitive or intimate information remains private until you match with someone emitting the same signals.
You may want a new job with certain characteristics like a salary threshold, experience level, location, etc. but can’t let your current employer know that you’re shopping. Your digital pheromones could link you with head hunters recruiting for jobs that match your description. A similar concept may exist for dating.
Or, you could post a tweet or a picture viewable only by people you met at a conference – or at burning man for that matter.
Cyberspace Manifest Destiny
Now that we’ve covered the first-order implications of graduating from specialized to generalized programmable cryptography and its applications, let’s talk about the longer term.
If these cryptographic protocols become sufficiently performant, they could permeate all digital activity. FHE replaces the S in HTTPS such that all data is encrypted at all times.

But it goes well beyond that. To experience how this cypherpunk future might unfold in its full potential, see this post that visualizes a future where ubiquitous general purpose cryptography is used to create a singular data layer, hallucinated servers, among other things.
Suffice to say that blockchains and programmable cryptography need each other. The former is an immutable, permissionless ledger – a single, universal database that could store all the world’s data and thus be perfectly composable. But they currently cannot allow for even remotely sensitive data so its applications are roughly limited to what they are today.
Meanwhile, programmable cryptography in its most powerful forms enables completely black box computing over private data to be done in plain sight – and be guaranteed to be done correctly. That’s a neat trick but not that useful if all data remains stuck in private clouds where it’s fairly safe but completely siloed.
In short, blockchains enable seamless composability while programmable cryptography instills care-free safety.
Apart from each other, they’re only so useful but together, they could herald a fundamentally new digital realm where all data is by default added to a composable black box. The socially-engrained mental habit of safeguarding sensitive data fades into a memory of a more primitive technological era when everything wasn’t encrypted end-to-end, everywhere, all the time, no matter what.
People become accustomed to freely moving their most sensitive secrets across permissionless, boundless digital worlds.
Digital barriers that arose for data privacy and security reasons no longer serve any purpose. Those walls fall like it’s 1989.
No more siloed data, no more breaches, and certainly no more HIPAA.
In this future where even private data can move freely around because all data is added to a private shared state that’s universal or perfectly composable with others, data moats and network effects completely dissolve. The friction of starting a better or different version of any data-oriented protocol from social media to life insurance falls rapidly to zero.
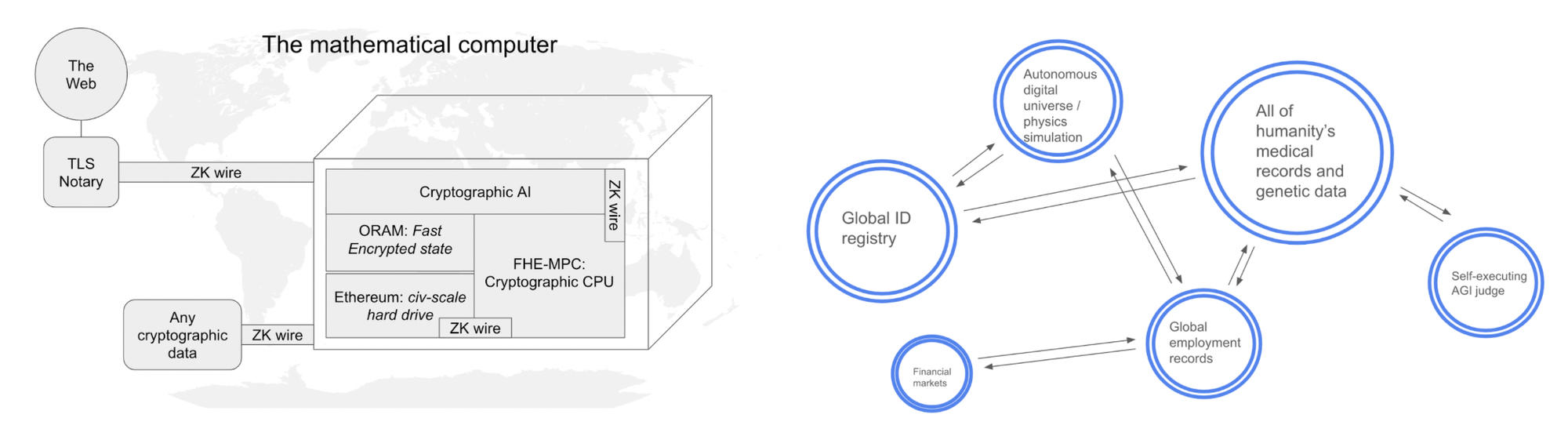
These visions are decade(s) ahead of their time. Today, both blockchains and general-purpose cryptography protocols are woefully slow and clunky. Like all disruptive technologies, they currently look more like toys than a threat to cloud infrastructure itself.

Maybe blockchains using programmable cryptography will never get performant enough. But, it would’ve been unimaginable to people in 1993 that today we express ourselves via 1MB GIFs instead of a three word text. But, because the cost of data transfer rapidly approached $0, the grotesqueness of a GIF being several OOM less efficient doesn’t even occur to those of us born in the iMessage era. A similar, multi-decade transformation happened as society adopted special-purpose cryptography. HTTPS evolved from banks buying $5K servers from Netscape to offer secure credit card processing in 1994 to HTTPS being used on all logins in 2005 to being the default for Gmail and public internet accesses in 2010 to securing 100% of internet activity today.

Maybe, in twenty years, the marginal cost of blockchains using programmable cryptography will become acceptably low such that even if it’s still far less efficient than AWS, that won’t even occur to those born in 2025 and the benefits of a seamlessly composable yet programmably private internet dominate.
It may be well off, but it’s a future worth dreaming about. And in the meantime, some incredibly exciting applications can be built.
Please reach out if you’re putting the cryptography back in crypto.